Introduction to Multi-Factor Authentication
As more of our information and login accounts are accessible on the Internet by anyone, criminals have developed sophisticated methods that enable them to guess your password, even if it's a relatively complex one. As a result, you have seen, or maybe experienced yourself, situations where an unknown individual is able to log in to someone's Facebook or Twitter account, or, worse, a business e-mail account. Once that happens, the bad actor can send apparently authentic messages as if they came from the victim, harming the reputation of the individual or his company, and potentially leading to financial loss.
Multi-factor authentication (MFA) can prevent criminals from getting into your account, even if they successfully guess your password. See, with a password only, all anyone has proven to the system that is handling your login attempt (which we'll call the "authenticating server") is that he knows the password. Authenticating servers can perform additional functions (that is, verify additional factors) to find out if it's you providing the password, and not a password thief. The most common method is to confirm you are in possession of a physical device that the authenticating server already knows you own.
![]()
When setting this up for the first time, typically you'll install an authenticator app on your phone or tablet from its usual app store, as directed by your IT manager. Icons for commonly used authenticator apps are depicted on the right.
Once that's done, the administrator of the system hosting the resource to be protected (such as your e-mail account) will configure the system to require multi-factor authentication. Then, the next time you log in, the authenticating server will have you register your mobile device to your account, using the authenticator app. This device will become what you must prove you have in your possession from now on.
The way you do this depends on the authenticating server. It can be as easy as responding to a prompt on your device asking if it's really you trying to log in, as depicted in the illustration below.
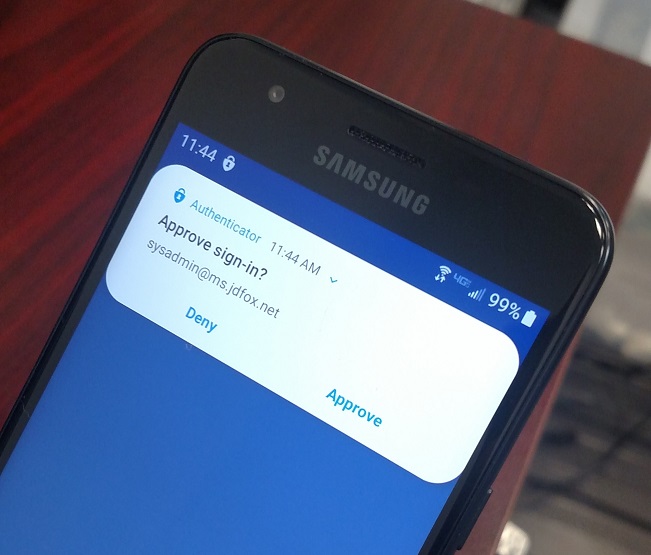
Once this is set up, then a criminal who guesses your password will not be able to get in. You can see why—when he enters your password and the authenticating server sends a prompt to your mobile device, you will reply indicating it was not you trying to log in. The criminal will be foiled.
You don't have to respond to a prompt on your phone every time you log in yourself, though. This is because every device or application you successfully use to log in will automatically be registered with your account. For example, when you log in to your e-mail using your desktop computer at work for the first time, you will get prompted on your mobile device, but from then on the computer will be recognized as yours by the authenticating server. So with your password saved as usual within your e-mail application (such as Microsoft Outlook), opening up your mailbox and getting to work will require no extra steps going forward, while your account remains much more secure.
This is not fool-proof, of course. If someone manages to trick you into confirming the prompt on your mobile device after guessing your password (or getting you to share it), he will gain access to your account. Vigilance will always remain an important component of information security, regardless of technological advances.
Let's now discuss mixing business and personal devices. Most businesses do not issue company-owned mobile devices to users, so when multi-factor authentication is implemented, employees use their personally owned devices. Although it's infrequent, some employees object, wishing not to connect their devices in any way to their employer's IT or cloud systems. One thing to understand is that registering the device for multi-factor authentication using an authenticator app does not log the user into his or her account from that device. So they won't start getting notifications on weekends from work e-mail, calendar reminders, or anything like that. It also does not give the business control over the device.
Some users simply don't have a mobile phone or tablet. In this case, or whenever a user has one but can't be persuaded to use it, the best solution is for the company to invest in a cheap tablet based on the Android operating system and issue it to the user for the sole purpose of multi-factor authentication.
Common public platforms are moving towards requiring multi-factor authentication. If systems you use for e-mail, file sharing, or line-of-business applications have announced that this will happen and you haven't planned to implement it, or if you're not sure, contact J.D. Fox Micro for help.